|
|
Program - Encryptor (Windows, Linux)
 Today, information is one of the main assets that ensures the livelihoods of people and the work of companies.
Today, information is one of the main assets that ensures the livelihoods of people and the work of companies.
Such information includes:
Logins and passwords for various Internet portals
Financial data (credit card numbers, PIN codes, online banking passwords, etc.)
Passport details
Photos or scanned documents
Other personal data
Our hard drives contain: addresses, phone numbers, photographs and videos, ideas, diaries, developments, collections of valuable materials, confidential information, passwords and pin codes.
|
- Cipher -
Version 4.0.
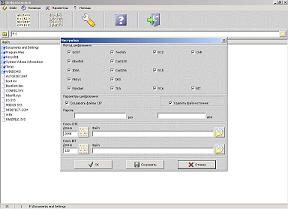
Program functions:
encryption and decryption of files using the GOST, Blowfish, IDEA, Misty1, Rijndael, Twofish, Cast128, Cast256, RC2, RC5, RC6, DES, TEA method using a password;
encryption and decryption of files using the CHR, BIT method using a key file;
selecting one or more encryption methods;
creating a separate encrypted file with the .cip extension;
complete deletion of the source file.
The program offers two options for saving the result of file encryption.
|
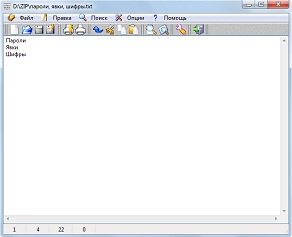
Confidential information is best stored in an encrypted text file.
The editor works with text in UNICODE format, so you can enter any characters, including hieroglyphs.
|
 .
.
|
The Encryptor software package will provide reliable cryptographic protection of your confidential data.
The main thing to remember is the encryption method(s) and password.
The encryption methods used in the program are quite reliable.
Remember - information needs reliable protection!
Many users write down their passwords and pin codes on pieces of paper, in the memory of PDAs and mobile phones, on flash drives and leave these records in places easily accessible to attackers.
We often face questions:
Many different passwords (for mail, for wallet, for something else).
You have confidential information (ideas, business developments): how can you reliably keep it from prying eyes?
I'm not the only one who uses a computer at the company.
You need to take the time to take care of the security of YOUR INFORMATION!
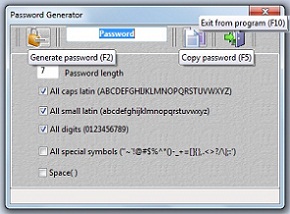
To solve this problem, a software package has been created: “File Encryptor”, “Cryptography Editor” and “Password Generator”.
|
|
|